
What is email fraud?
If you have had an email address for a decent amount of time, chances are that you have probably dealt with at least one suspicious email- but, most likely, you’ve seen a substantial number of them. Email fraud can come in many forms. They are used to install malware onto the recipient’s computer through suspicious links and files to gain information, or they can fool a consumer into outright offering his or her usernames, passwords, personal information (like a Social Security Number and answers to common security questions), or money through online transfers.
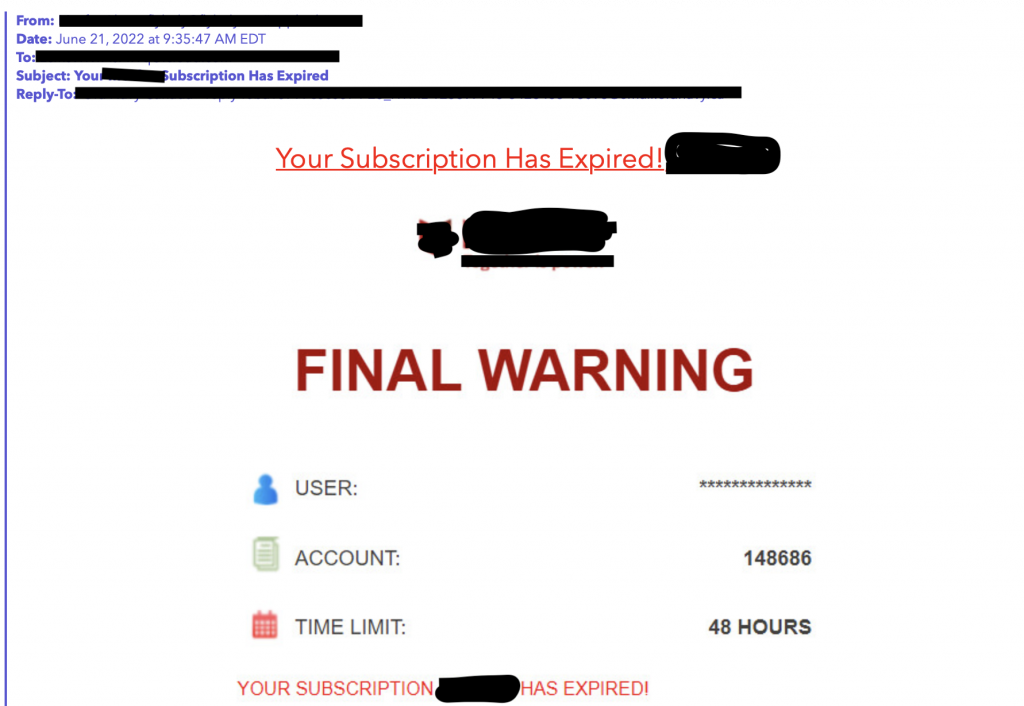
When a malicious email pretends to be from a reputable company, it is considered “phishing” or a BEC (business email compromise). Criminals use a tactic called “spoofing”, which means they try to replicate the legitimate company’s marketing style to target loyal supporters. All organizations are susceptible to being impersonated with these BECs, from retailers to banks. Even charities can be targeted. When was the last time you received an email that looked suspicious from a company you know?
According to alta.org, BEC schemes are the costliest when it comes to fraud, resulting in losses of $1.8 billion in the year 2020 alone (United States).
MORE RAMPANT THAN EVER BEFORE
Think for a moment- how often do you see these emails today compared to 5 years ago?
Businesswire.com points out that the Covid-19 pandemic “changed consumer behavior”. Because of the stay-at-home order, people heavily relied on technology to make their purchases. Just think about the boom of online banking, deliveries, and streaming services. Since consumers were forced to switch to digital transactions, there were sudden changes that companies had to adhere to in order to stay afloat- and criminals took full advantage of this unfamiliar digital chaos (especially when a business went under, but their customers were unaware of the news).
The public also had an increased online presence, leading to more opportunities for scams. Email isn’t the only way for phishing to happen. Cyberattackers can pop up in robocalls, texts, and social media (see this article for more information on how we can detect fake accounts), but as we read previously, phishing through email is more common and more costly.
COMMON TARGETS & TACTICS
If someone is old enough to have an online account, they are susceptible to fraudulent emails. Anyone can be a recipient for any kind of attack, but there can be patterns depending on a person’s age group.
Kids and teenagers tend to be targeted with social media, video games, chatting applications, and their favorite brands. They can be drawn in by the idea of a free/exclusive item, whether a physical gift or digital. For example, an email could appear with a suspicious link, claiming that clicking will enter them in a raffle for the newest iPhone. Or maybe the email states they’ve won in-game currency, and they need to give up sensitive information to obtain it.
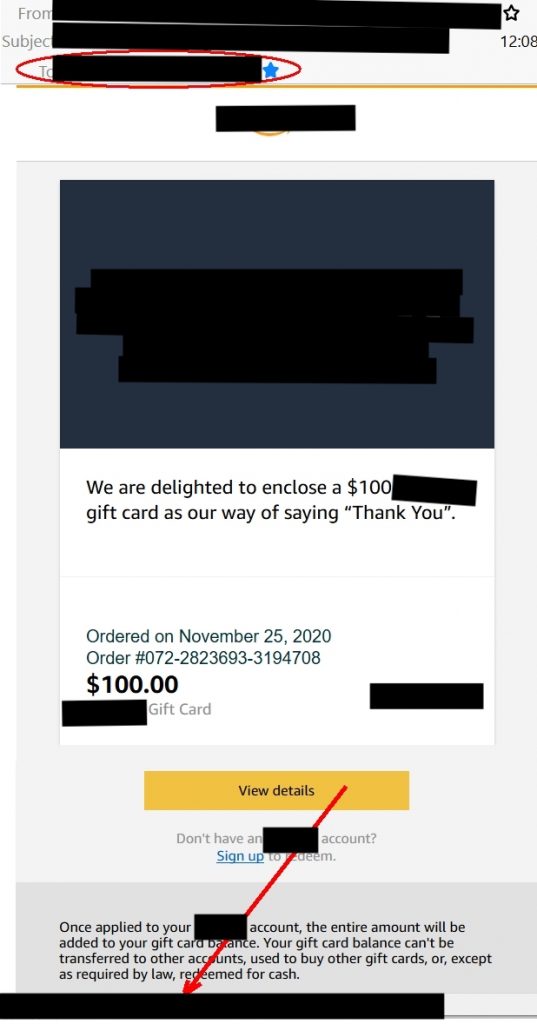
Younger and middle-aged adults, who have grown up during the development of modern technology, are usually targeted with more subtle scams. These can consist of rewards from stores they frequently visit, money transfer confirmations, and links to check on their scheduled deliveries. Most people have probably come across an email that congratulates them on their new $50 gift card from a specific digital marketplace.
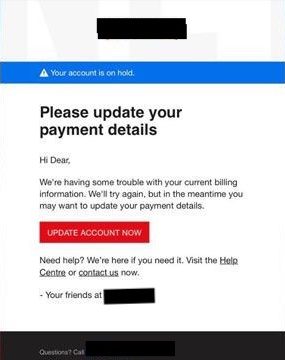
Older folks can be pressured into quickly responding to an “urgent” message about their health, insurance coverage, finances, or other disconcerting information. A common tactic is to manipulate the person into feeling rushed or like something bad may happen if they delay a response for any reason, giving them less time to practically think about what they are sending, downloading, or clicking on.
Have you had anyone in your life who has told you about receiving a phishing email?
WHAT CURRENT AUTHENTICATION MEASURES CANNOT DETECT
There is a plethora of security measures that websites use to protect their users and their brand from receiving or being replicated by BECs. However, these are majorly text-based, and focus on the presence of links, the way an email address is spelled, or the written contents inside the email. Many scams still slip through the cracks, allowing malicious emails to end up in inboxes every day, several times a day.
What does your business do currently to ensure phishing prevention?
What is currently needed is an image comparison system that also sorts through these emails, and swiftly detects the suspicious images that other systems are unable to view. DejaVuAI can add this new level of verification. With our system, it is easy for us to detect if a logo is slightly “off”- such as it being slanted, missing a trademark logo, or stretched out.
If a brand is looking to protect their consumers and their reputation, they could offer us a list of approved emails. With this, we can alert them of what non-approved email addresses are using exact copies of their logo.
People are embracing more complex authentication in order to keep their info out of the hand of cybercriminals. What’s great about our system is that it’s another layer of added security, but it doesn’t feel intrusive or time-consuming to the users (like authentication with text alerts and emails can sometimes feel). Our tech will do all the work for you- and you can rest, knowing that you have the best image recognition software on your side.
Don’t forget to report any suspicious emails you receive! Let your email provider know. You can also report to the Federal Trade Commission or The Internet Crime Complaint Center.
Follow us on LinkedIn, Facebook, Twitter, YouTube and Instagram for updates. Or feel free to send us an email!